Digital Maturity Assessment

Know Yourself!
With the advancements in technology, the current state of information technologies has increased the necessity for organizations to “assess themselves". Due to security vulnerabilities, companies are experiencing significant data losses, and these irreparable losses lead to damage in reputation, time, and financial resources.
Through DMA an independent assessment is bprovided for your organization's cybersecurity. It is based on standards such as ISO 27001, frameworks like COBIT, and CIS control lists, taking into account technical analyses for verification. It enables the scoring of the Information Technologies infrastructure froma different professional perspective’ and our technical teams in various disciplines conduct examinations using different methods and devices.
THE 4 KEY ELEMENTS OF DMA



MATURITY
ASSESSMENT

Two-thirds of information technology projects end in failure.
MCKinsey
The annual damage from known ransomware attacks exceeds $20 billion.
CISQ
Cyber threats incur a total annual cost of $7 trillion, equivalent to 1% of the global GDP
FBI
Over the past three years, 66% of organizations have faced significant issues in their information technology.
FBI
Despite the presence of numerous cybersecurity products, organizations continue to experience serious vulnerabilities.
The effective functioning and compatibility of software, hardware, and security components within a company's IT infrastructure are crucial for resilience against current threats.
Human error is often the root cause of these vulnerabilities.
Rather than implementing small-scale controls, DMA entails a comprehensive analysis process that encompasses all stakeholders within the organization.

HOW DOES DMA WORK?

IT REGULATORY CONTROLS
Information Technology regulations have been developed to identify all risks and assess compliance with best practices. All standards are a transfer of experience and are crucial. Information security must be controlled from the perspective of regulatory compliance.
- IT Governance Analysis (COBIT) Example COBIT Analysis
- IT Information Security Analysis (ISO 27001, NIST CSF, CIS)
- CB DDO Information and Communication Security Guide Analysis
- IT Service Management Analysis (ITIL, ISO 20000-1)
- IT Business Continuity Analysis (ISO 22301)
- Software Life Cycle Analysis (CMMI)

Methods / Tools Used
- Infrastructure Control Software
- Analysis Hardware
- Question / Answer
- Pentest Tools
- Configuration Review
- Cyber Threat Intelligence
- Content Indexing and Crawling Software
- Scoring Software
TECHNICAL COMPLIANCE CHECKS
It enables the Information Technologies infrastructure to be scored from a different, professional perspective. Expert technical teams from different disciplines carry out examinations using different methods and devices.
- Server, Storage and Virtualization Systems Analysis
- Network Analysis
- Cyber Security Infrastructure Analysis
- Basic Vulnerability Scanning
- Cyber Threat Intelligence
- Data and Database Analysis
- SIEM Analysis
- Content Scanning
- Web Page Control
- Archive Analysis
- IT Infrastructure Scoring

IT SCORING
BThe entirety of processes preventing unauthorized and unauthorized alteration or damage to information is referred to as "Information Security." The secure storage of information is ensured by ISO 27001.
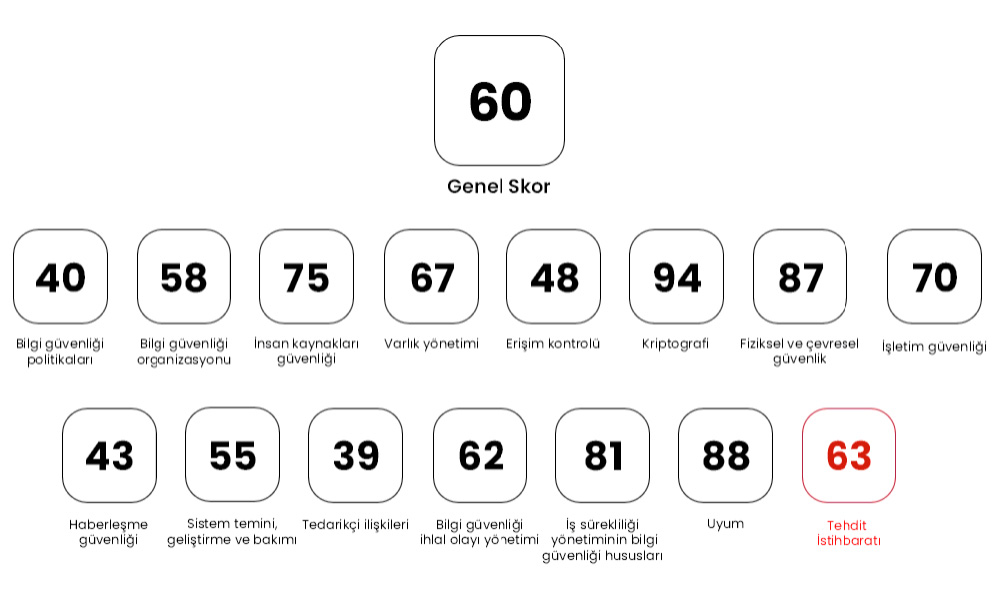
- Scoring under ISO 27001 covers 14 categories::
- Information security policies
- Information security organization
- Human resource security
- Asset management
- Access control
- Cryptography
- Physical and environmental security
- Operational security
- Communication security
- System acquisition, development and maintenance
- Supplier relationships
- Information security incident management
- Information security aspects of business continuity management
- Compliance
- Personnel Awareness Control

FINDINGS AND ROADMAP REPORTS
Digital Maturity Assessment evaluates and reports on the maturity of the information system infrastructure in institutions from an end-to-end regulatory perspective. The provided report includes the following sections:
- Executive Summary
- Detailed findings and recommendations report
- Roadmapı
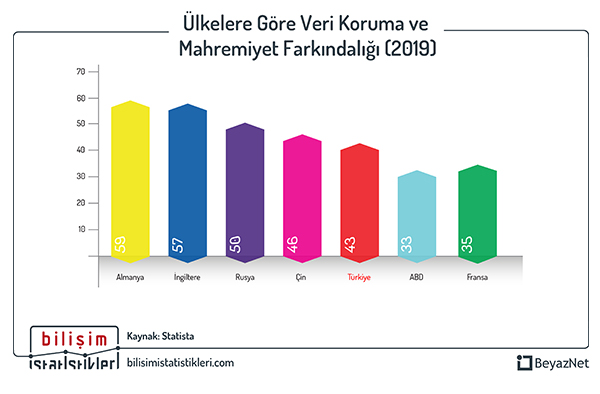
NUMERICAL DATA ON DMA
OUR DMA REFERANCES